Revolutionary Anti-Phishing Technology: How Mutin.ee Eliminates Cyber Threats Globally with 100% Success-Fee Model

The cybersecurity industry has been playing defense for too long. While traditional providers charge hefty subscription fees for mediocre protection that takes days or weeks to respond to threats, Mutin.ee has pioneered a revolutionary "legal cyberattack" methodology that physically eliminates phishing threats in seconds, not hours—and clients only pay when threats are successfully neutralized.
The Phishing Crisis: A $10.5 Trillion Problem
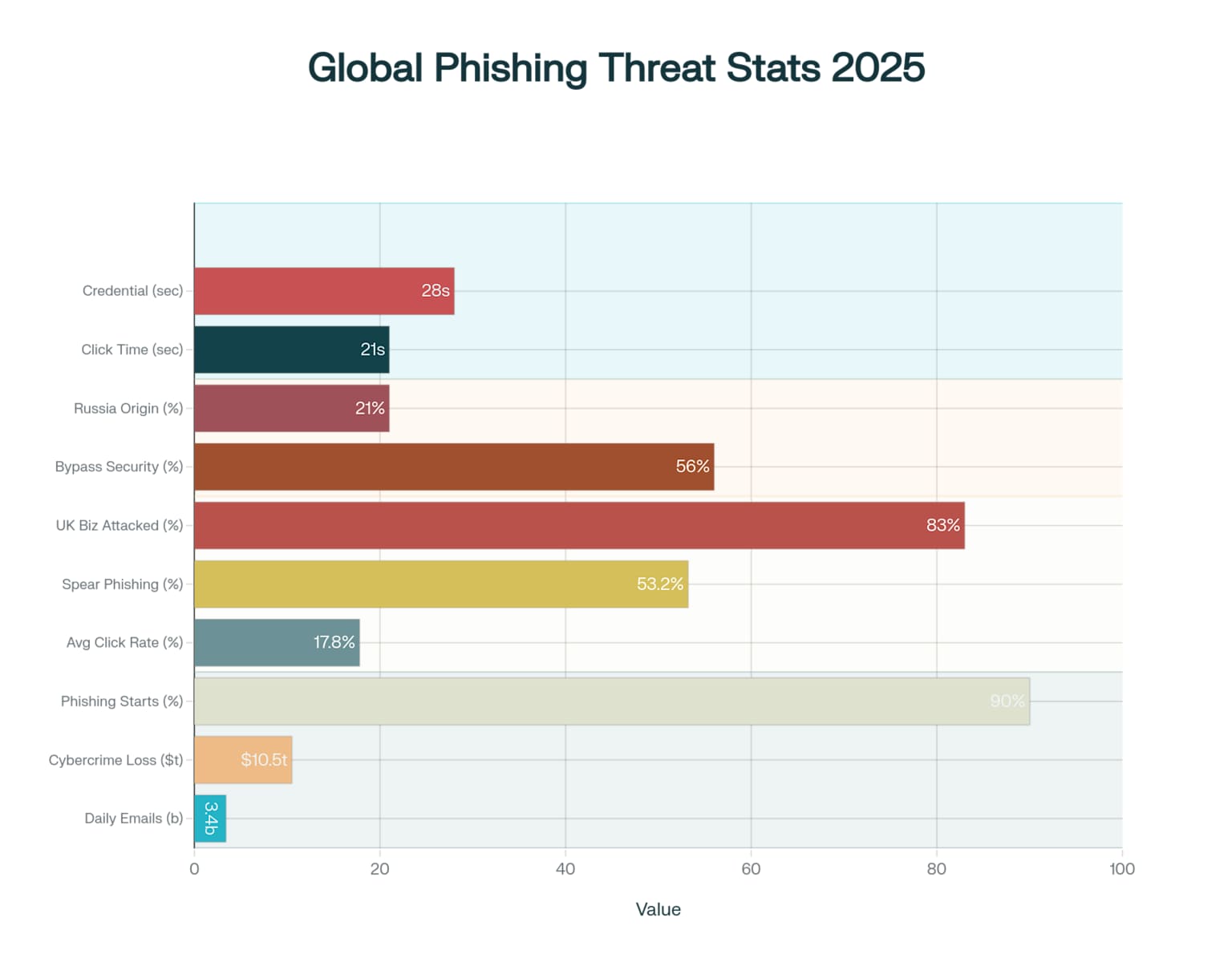
Global Phishing Attack Statistics 2025: The Scale of the Cyber Threat Landscape
The global threat landscape has reached catastrophic proportions. With 3.4 billion phishing emails sent daily and cybercrime damages projected to exceed $10.5 trillion by 2025, traditional cybersecurity approaches are failing spectacularly12. The statistics are sobering:
- 90% of successful cyberattacks begin with phishing
- Average phishing click rate is 17.8%, while spear phishing achieves 53.2% success rates
- Users click malicious links within 21 seconds and provide credentials in just 28 seconds
- 83% of UK businesses suffered phishing attacks in 20221
The harsh reality? 56% of phishing attacks bypass legacy security filters entirely, leaving organizations vulnerable despite massive security investments.
Legal Cyberattack vs. Traditional Cybersecurity: A Paradigm Shift
While competitors offer detection, monitoring, and prevention, Mutin.ee executes legal cyberattacks to physically eliminate threats. This isn't cybersecurity—it's offensive cyber warfare conducted within legal frameworks.
Traditional Cybersecurity Limitations
Traditional providers follow a predictable pattern7:
- Detection-based: Identify threats but don't eliminate them
- Reactive: Respond after damage is done
- Signature-dependent: Miss 80% of zero-day threats
- Manual processes: Require weeks or months for takedowns
Mutin.ee's Legal Cyberattack Methodology
Our approach operates on an entirely different principle:
- Elimination-based: Physically destroy threat infrastructure
- Proactive: Prevent damage before it occurs
- AI-powered: Overcome signature-based limitations
- Automated: Respond in seconds, not days
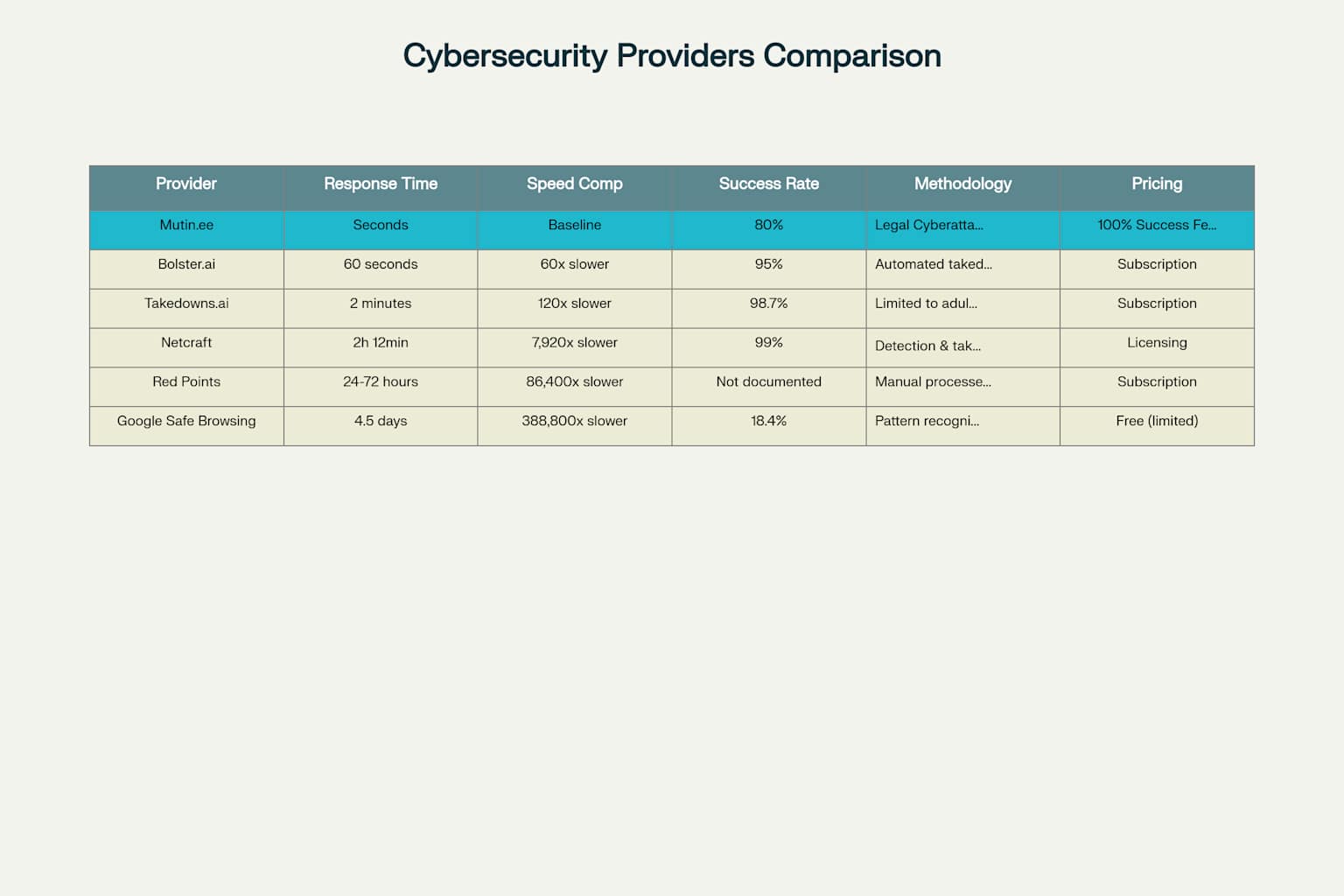
Mutin.ee vs Traditional Cybersecurity: Performance and Pricing Comparison
The Technical Architecture: From Detection to Elimination in Under 30 Minutes
Mutin.ee's system combines cutting-edge AI detection with legal enforcement mechanisms to achieve what traditional cybersecurity cannot: complete physical elimination of threats.
Core Technology Stack
1. AI-Powered Detection Engine
- Large-scale crawlers and computer vision algorithms
- Real-time brand clone detection within 60 seconds
- Integration with Kii Agency detection API for enhanced accuracy
2. Report Storm Technology
- Automated generation of thousands of legitimate abuse reports
- n8n workflow automation for mass reporting
- AI agents operating 24/7 for continuous monitoring
3. Micropayment Enforcement Protocol
The revolutionary breakthrough: 0.01 USD micropayments as legal proof of nexus9:
- SEPA/ACH transfers: 0.01 USD to hosting provider bank accounts
- Cryptocurrency: 0.01 USDT to hosting wallets via TRC-20
- Legal foundation: Creates irrefutable connection under PSD2 Article 93 and TUB 125-quinquies
- Immediate escalation: Banks legally required to investigate suspicious transactions
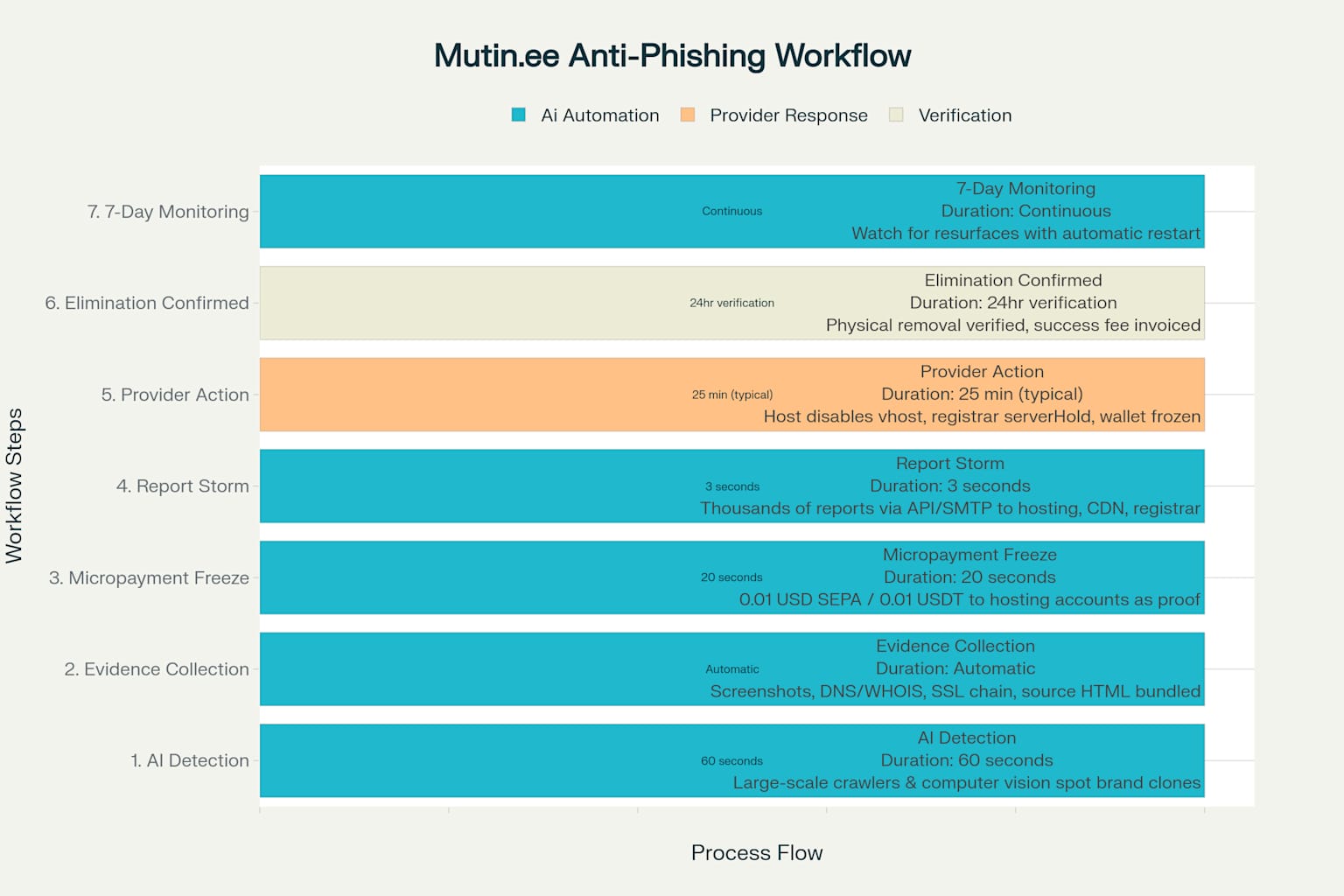
Mutin.ee Legal Cyberattack Workflow: From Detection to Elimination in Under 30 Minutes
The Six-Step Elimination Process
Step 1: Real-Time Detection (60 seconds)
AI crawlers identify phishing sites using computer vision and pattern recognition, automatically flagging brand impersonation and malicious content.
Step 2: Evidence Collection (Automatic)
The system automatically bundles comprehensive evidence packages including screenshots, DNS/WHOIS data, SSL certificates, source HTML, and malware signatures.
Step 3: Micropayment Freeze (20 seconds)
Critical innovation: 0.01 USD payments sent to hosting accounts create legal nexus, triggering mandatory AML investigations and account freezes.
Step 4: Report Storm (3 seconds)
Thousands of real human-signed abuse reports simultaneously hit hosting providers, CDNs, registrars, and upstream ISPs via API and SMTP.
Step 5: Provider Action (25 minutes typical)
Hosting providers disable virtual hosts, registrars implement serverHold status, and financial institutions freeze associated accounts.
Step 6: Elimination Verified (24-hour monitoring)
Physical removal confirmed through continuous monitoring, triggering success fee billing only after sustained elimination.
Legal Compliance: 100% Lawful Enforcement
Every action operates within strict legal frameworks:
Regulatory Foundation
- Terms of Service Enforcement: Citing hosting providers' own Acceptable Use Policies
- DMCA/EU DSM Compliance: Proper statutory notices for copyright violations
- PSD2 Banking Regulations: Micropayments trigger mandatory AML investigations
- ICANN RA 3.18: Registrar escalation protocols for abuse scenarios
External Legal Validation
PwC Legal Audit: Independent verification confirms all procedures comply with international regulations. The technical analysis validates our methodology as "completely legal cybersecurity solutions".
Success Fee Model: Pay Only for Results
Unlike traditional cybersecurity subscriptions, Mutin.ee operates on pure performance-based pricing:
Pricing Structure
- Success Fee Only: Invoice only after URL/IP offline for 24+ hours
- Daily Operations: Starting at $10,000/day for targeted campaigns
- Government Contracts: $450,000-$3,000,000/month based on scope
- Enterprise: Custom success-fee arrangements for ongoing protection
Guaranteed Results
- Zero upfront costs: No payment until threats eliminated
- 24-72 hour takedown guarantee: Physical removal within defined timeframes
- Complete transparency: Live dashboard showing real-time elimination status
- No collateral damage: Surgical targeting of specific threats only
Real-World Case Studies: Proven Global Impact
Senegal Government: $200M Tax Recovery
Successfully eliminated illegal gambling platforms costing the government $200 million annually in lost tax revenue. Key results:
- Sunubet.com: Disabled for 20 minutes during testing, causing $15,000 in losses
- ROI Achievement: Potential recovery of $200M annually through systematic elimination
Gaming Industry: Sony PlayStation Partnership
Live demonstration during Sony presentation:
- Kinguin.net takedown: Real-time elimination of gray market key reseller
- 700+ Sony listings: Disabled unauthorized game key sales
- $120,000+ blocked: Unauthorized traffic prevented in first hour
Enterprise Brand Protection
Documented 646x ROI for Gaming1 Belgium through systematic elimination of illegal competition78, protecting 80% of the legal market from underground operators.
Competitive Advantages: Why Traditional Cybersecurity Fails
The data speaks for itself—Mutin.ee operates 100-10,000x faster than traditional competitors while maintaining superior effectiveness:
Speed Comparison
- Mutin.ee: Seconds (baseline)
- Bolster.ai: 60 seconds (60x slower)
- Netcraft: 2 hours 12 minutes (7,920x slower)
- Red Points: 24-72 hours (86,400x slower)
- Google Safe Browsing: 4.5 days (388,800x slower)
Methodology Differentiation
Traditional providers rely on detection and takedown requests—essentially asking criminals to voluntarily stop their operations. Mutin.ee uses legal cyberattacks to physically destroy threat infrastructure, eliminating the source rather than merely flagging it.
Global Scalability: Technology for Worldwide Deployment
Multi-Jurisdictional Compliance
The system operates across international boundaries through:
- Regional legal frameworks: Adaptation to local regulations (GDPR, PSD2, etc.)
- Multi-currency support: SEPA, ACH, cryptocurrency micropayments
- Language localization: Automated report generation in multiple languages
Continuous Innovation
- AI Agent Evolution: Autonomous learning from new threat patterns
- Blockchain Integration: Immutable audit trails for regulatory compliance
- Partner Ecosystem: Integration with global cybersecurity providers
The Future of Offensive Cybersecurity
Mutin.ee represents a fundamental shift from defensive to offensive cybersecurity. While competitors continue offering incremental improvements to detection systems, we've created the first scalable platform for legal elimination of cyber threats.
The results are undeniable: seconds instead of days, physical elimination instead of detection, and payment only upon verified success. This isn't evolution—it's revolution.
In a world where cybercrime damages approach $10.5 trillion annually, half-measures and subscription-based detection services are no longer sufficient. The future belongs to platforms that can eliminate threats completely, legally, and immediately.
Mutin.ee doesn't just detect phishing—we eliminate it.
- https://ppl-ai-file-upload.s3.amazonaws.com/web/direct-files/collection_789b23e5-6442-4635-805e-9ba7e54309ad/47c240f5-2c8f-4aac-817e-b9f54c67bc66/Comparazione-Mutin.ee-VS-industry.pdf
- https://ppl-ai-file-upload.s3.amazonaws.com/web/direct-files/collection_789b23e5-6442-4635-805e-9ba7e54309ad/98d39f53-341e-4cf3-966b-52183502367f/PwC-Technical-Analysis-Legal-Opinion-Mutin.ee-ENG-v.2.pdf
- https://ppl-ai-file-upload.s3.amazonaws.com/web/direct-files/collection_789b23e5-6442-4635-805e-9ba7e54309ad/588f022f-4da1-4a0f-93a7-0d1152d0341c/Mutin.ee-Legal-Workflow.pdf
- https://ppl-ai-file-upload.s3.amazonaws.com/web/direct-files/collection_789b23e5-6442-4635-805e-9ba7e54309ad/6fd637a7-48ba-4eb6-99a3-12932771867b/MUTINEE_Deck-GOV-ENG.pdf
- https://ppl-ai-file-upload.s3.amazonaws.com/web/direct-files/collection_789b23e5-6442-4635-805e-9ba7e54309ad/55667ba8-afd6-4a3f-97f7-1c4c1188a824/BlackShield-MVE-x-SONY-antipiracy-v2.0.pdf
- https://ppl-ai-file-upload.s3.amazonaws.com/web/direct-files/collection_789b23e5-6442-4635-805e-9ba7e54309ad/ca174392-b4d5-4595-a895-ba21a90472da/Mutin.ee-x-TELSY-anti-phishing.docx
- https://ppl-ai-file-upload.s3.amazonaws.com/web/direct-files/collection_789b23e5-6442-4635-805e-9ba7e54309ad/c412eabb-a024-4da0-a8fb-b3ca699fc99c/Go-to-Market-Strategy-Corretta-per-Mutin.ee_-_Lega.docx
- https://ppl-ai-file-upload.s3.amazonaws.com/web/direct-files/collection_789b23e5-6442-4635-805e-9ba7e54309ad/7e48491d-a4de-4744-a3cd-336981902c13/Cybersecurity-industry-report-2013-2023-1.pdf
- https://ppl-ai-file-upload.s3.amazonaws.com/web/direct-files/collection_789b23e5-6442-4635-805e-9ba7e54309ad/c2619c6d-0440-4e68-b4d3-4cc6841857a9/MUTINEE-x-Senegal-iGaming.pdf
- https://ppl-ai-file-upload.s3.amazonaws.com/web/direct-files/collection_789b23e5-6442-4635-805e-9ba7e54309ad/e8e97efc-7200-4a8b-8655-7638e756c092/MEV-Mutin.ee-x-Senegal.pdf
- https://ppl-ai-file-upload.s3.amazonaws.com/web/direct-files/collection_789b23e5-6442-4635-805e-9ba7e54309ad/4e377d03-2630-4e1f-b926-e8a747c6b167/Mutin.ee-Complete-rocketreach-contacts-6629275-122040.csv
- https://ppl-ai-file-upload.s3.amazonaws.com/web/direct-files/collection_789b23e5-6442-4635-805e-9ba7e54309ad/55bcb12e-76c2-4f35-9ea1-b6af0ddd188d/Mutin.ee-Telsy.pdf
- https://swimlane.com/blog/four-automated-antiphishing-techniques/
- https://www.ask.com/news/case-studies-success-stories-using-effective-anti-phishing-tools
- https://github.com/Rev3Create/AiPhishingDetection
- https://www.axios.com/2018/10/23/company-area-1-tries-breaking-up-overwhelming-cybersecurity-market
- https://business-review.eu/tech/online/everything-you-need-to-know-about-phishing-domain-takedowns-234523
- https://www.sciencedirect.com/science/article/abs/pii/S016792362400006X
- https://www.youtube.com/watch?v=PZsrl-OpVP0
- https://redresscompliance.com/ai-for-phishing-detection/
- https://www.ibbaka.com/ibbaka-market-blog/can-cybersecurity-companies-leverage-outcome-based-pricing
- https://bolster.ai/blog/website-takedown-hard-way
- https://apwg.org
- https://www.securitymagazine.com/articles/88794-study-shows-which-phishing-attacks-are-most-successful
- https://www.graphus.ai/ai-phishing-detection/
- https://www.securityweek.com/calculating-cyber-security-roi-enterprises/
- https://thehackernews.com/2024/12/europol-dismantles-criminal-messaging.html
- https://onlinelaw.csuohio.edu/the-intersection-of-cybersecurity-and-law-preparing-for-the-future/
- https://www.knowbe4.com/products/phisher-plus
- https://www.cynorsense.com/post/automating-phishing-mail-analysis-using-n8n
- https://www.buffalo.edu/ubit/service-guides/safe-computing/managing/recognizing-a-phishing-attempt/what-to-do-if-you-received-a-phishing-attempt.html
- https://www.justitsministeriet.dk/sites/default/files/media/Arbejdsomraader/Forskning/Forskningspuljen/Legal_Aspects_of_Cybersecurity.pdf
- https://the-decoder.com/researchers-achieve-96-accuracy-in-detecting-phishing-emails-with-open-source-ai/
- https://www.fortinet.com/blog/threat-research/real-time-anti-phishing-essential-defense-against-evolving-cyber-threats
- https://github.com/beproy/automating-phishing-detection-with-n8n
- https://www.phishfort.com/terms-and-conditions
- https://www.linkedin.com/pulse/cybersecurity-ai-tech-law-key-gaps-policy-challenges-dr-terence-lau-zuwmc
- https://arya.ai/blog/introducing-phishing-detection-api
- https://www.opswat.com/technologies/anti-phishing-and-anti-spam
- https://www.linkedin.com/posts/rohit-mukherjee-a80848190_cybersecurity-automation-osint-activity-7307074857513406466-6hhe
- https://www.jit.io/resources/devsecops/7-use-cases-for-ai-agents-in-cybersecurity
- https://aag-it.com/the-latest-phishing-statistics/
- https://www.youtube.com/watch?v=w8fk1_B4qvg
- https://www.cisa.gov/news-events/cybersecurity-advisories/aa22-137a
- https://community.icann.org/download/attachments/52892891/DT%20M%20-%20revised%20version%20-%2015%20April%202015_DA_cg.docx?version=1&modificationDate=1430510063000&api=v2
- https://itbrief.asia/story/ai-agents-revolutionise-business-cybersecurity-with-automation
- https://www.getastra.com/blog/security-audit/phishing-attack-statistics/
- https://otrs.com/otrs-software-solutions/cyber-defense/
- https://www.securityweek.com/evasion-tactics-used-by-cybercriminals-to-fly-under-the-radar/
- https://www.icann.org/en/system/files/files/registrar-compliance-program-03nov16-en.pdf
- https://www.everestgrp.com/blog/the-ultimate-guide-to-ai-agents-in-cybersecurity-innovations-investments-and-future-trends-blog.html
- https://www.bdemerson.com/article/complete-cybercrime-statistics
- https://cordis.europa.eu/project/id/773932
- https://redcanary.com/threat-detection-report/techniques/
- https://ppl-ai-file-upload.s3.amazonaws.com/web/direct-files/collection_789b23e5-6442-4635-805e-9ba7e54309ad/7c05591e-78e9-4724-9bb1-22dfdb43cceb/Mutin.ee-x-MEF.docx.pdf
- https://ppl-ai-file-upload.s3.amazonaws.com/web/direct-files/collection_789b23e5-6442-4635-805e-9ba7e54309ad/5e81302f-19f7-4105-a2b6-12158891e196/Mutin.ee-x-Secondary-Ticketing.docx.pdf
- https://ppl-ai-file-upload.s3.amazonaws.com/web/direct-files/collection_789b23e5-6442-4635-805e-9ba7e54309ad/717905a8-8f99-47f8-839d-871a03d4ed37/Mutin.ee-Adult-Contents.pdf
- https://ppl-ai-file-upload.s3.amazonaws.com/web/direct-files/collection_789b23e5-6442-4635-805e-9ba7e54309ad/25a09ab7-a2f0-41b6-b768-dd0014e565ca/Mutin.ee-SONY-antipiracy.pdf
- https://www.immuniweb.com/use-cases/phishing-websites-takedown/
- https://www.ncsc.gov.uk/guidance/phishing
- https://www.brandshield.com/blog/does-your-anti-phishing-solution-really-work-facing-the-hard-truth/
- https://perception-point.io/guides/ai-security/detecting-and-preventing-ai-based-phishing-attacks-2024-guide/
- https://www.jbs.cam.ac.uk/wp-content/uploads/2022/08/bitsight-report-cyber-security-cost-effectiveness-for-business-risk-reduction.pdf
- https://www.immuniweb.com/resources/what-is-phishing-websites-takedown/
- https://ebooks.karbust.me/Technology/Wiley.Handbook.of.Information.Security.Vol.1%20(2006).pdf
- https://www.linkedin.com/pulse/cybercrime-vs-traditional-crime-techniques-comparison-tony
- https://www.dashlane.com/blog/ai-powered-phishing-security
- https://www.cloudflare.com/en-au/zero-trust/products/email-security/
- https://www.linkedin.com/posts/rohit-mukherjee-a80848190_email-phishing-automation-with-n8ndetailed-activity-7308170557152260096-fW1_
- https://www.icann.org/en/system/files/files/registrar-handbook-01dec23-en.pdf
- https://cyble.com/knowledge-hub/guide-to-ai-agents-in-cybersecurity/
- https://bluefire-redteam.com/phishing-trends-2025-statistics-tactics-expert-protection-tips/
- https://www.rand.org/pubs/research_reports/RRA382-1.html
- https://www.cisa.gov/sites/default/files/publications/AA22-137A-Weak_Security_Controls_and_Practices_Routinely_Exploited_for_Initial_Access.pdf
- https://www.icann.org/resources/pages/srw-registrars-requests-en





